In this and the next Post’s I will bring you a little light in the curiosities of all the short cuts of words the we all generated in the last past years for Mobile Devices. This Post describes my own view of that all, it is like a little collection of questions that I have to answer on Customers and Trainings I had.
In this Case I have not only the technical perspective, this Post could also help the Management to understand what points are important and what example or case will struggle the whole Project.
To Understand, I begin with the Concept/Process and then prepare the Application selection and the Application Layer. After that we can start to configure the App/SW we selected to use!
This is just my view and you can interpret your own to Use… I hope I can bring a little Sun to the horizon in the “rainy”-cloud. Of course my prospective are with Microsoft glasses, I love my Job, I knew a little more then the Border’s but MS is my favorite.
What we have and we like to have, is like a PLAN that we have to generate before we can start with a Project, in this case is it the same that we are success in the end, right?
Or is it possible to drive a racing track with a Tank, yes it is, but maybe once and not the whole day to enjoy, better you bring the right car to a race track.
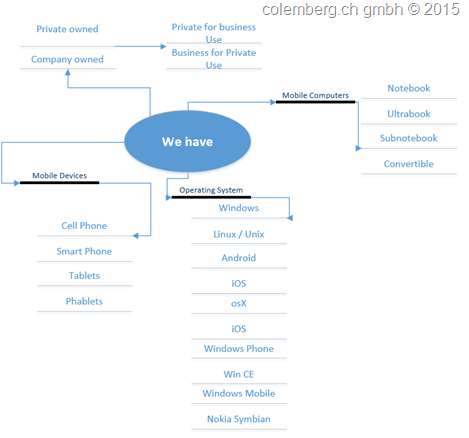
1. we have a Brainstorming about “we have”
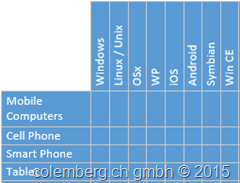
2. What is a possible configuration between OS and HW
This is just an example to show you what you have to think about, this can be bigger or smaller but it’s important for a later use in the Application Layer we will use after we create some Processes to show where the way will go.
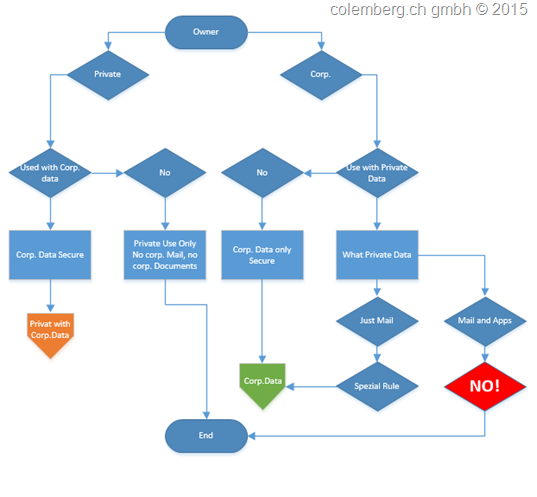
3. We need a Process flow to control what we want
Yes, what we want to support in Our Environment, that means the same we have for Our Computers in the Infrastructure to manage! (As an example for Our Computers; had User’s Local admin rights, if yes, why / We have different Support Users like VIP-Support and normal Support…)
In this Case we will clarify BYOD (Bring your Own “Device”)
Yes or No, this is important that you have a little matrix to say what we want to support, this is simple, maybe too simple for some Companies to understand that, in the end, the Support time of all what is allowed can grow to a …. really expensive Case
In the Beginning of the Process we have to clarify who brings the Device, here we speak about the Mobile Devices like Cellphones, Smartphones and Tablets (all the devices you can call in the classic way another person)
You can See the Big red NO!, that way ends in a Expensive Case, you have no control what the User Install or Configure on a Company Device, it is a Company Device, what you think where the Employee go’s to call for Support –> your Organization-Support, have you time for that –> NO! if yes have you the money and time to Support this –> “give you the answer self”
With some simple questions we end in Tree Scenarios:
- Private Device with Corporate Data On it
- Corporate Device with Corporate Data and maximum support Private Mails, Calendar and Contacts
- Private Only –>End, Corporate Device to play for Private –> End
Do not understand me wrong, if you have the “NO!” case, then you have two options, to make your employee happy, sponsor him a Device and use the Private Device Path or the User have to use two Devices a Private and a Business one. That’s not a big Deal to organize a Device but in this case we speak about the Management for Devices that make sense and not a mess.
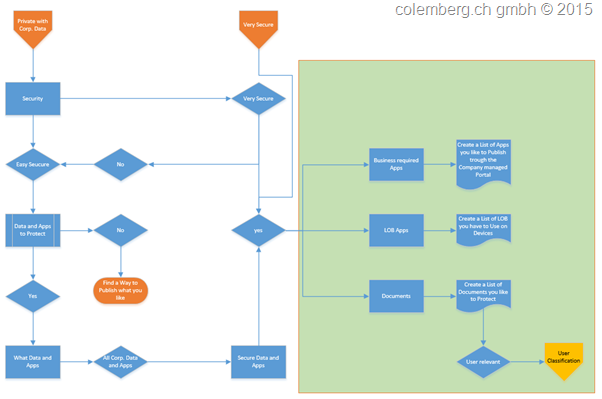
4. Security, How Secure is important for us
What means that, “ how Secure is important” Security is always important, of course.
Maybe we have different Aspects of Users in Our Environment, Like CEO, HR, Marketing, …
All this different Business requirements generates different Data’s, now we have to find a way which one we would like protect and which Data are not that much interesting to Protect.
This ends in a Data Classification and also User Classification that we can go forward to a next level.
For the User Classification and the next Step’s I will Post this in the next Time, hope you come Back soon to read more.
Leave a Reply