Have you seen in Windows 10 Technical Preview Build 240 what’s going on with the Windows Update Logs what you known in older Days of Windows.
You can still find a WindowsUpdate.log in C:\Windows
OK we will see the link they give us https://support.microsoft.com/en-us/kb/3036646
This opens a new Site that’s calling “How to read the new Windows Update log in Windows 10 Insider Preview” interesting in my end, ok follow the steps; (C&P from the Site)
- Download the public symbols by following the directions here. Install these symbols to a directory such as C:\symbols.
- Download the Tracefmt.exe tool by following the instructions here.
- Open a command prompt with administrative rights.
- Create a temporary folder, such as %systemdrive%\WULogs.
- Locate the directory that contains Tracefmt.exe, as downloaded and installed in step 2. Then, copy Tracefmt.exe to %systemdrive%\WULogs.
- Run the following commands at a command prompt, in the order presented:
- cd /d %systemdrive%\WULogs
- copy %windir%\Logs\WindowsUpdate\* %systemdrive%\WULogs\
- tracefmt.exe -o windowsupate.log <each windows update log delimited by space> -r c:\Symbols
For example, the last line might resemble the following:
tracefmt.exe -o windowsupate.log Windowsupdate.103937.1.etl Windowsupdate.103937.10.etl -r c:\Symbols
Ok let’s do this in real (that description doesn’t really work):
Go to the public symbols
1. In the Public Symbols part we have 4 Options to use them: https://support.microsoft.com/en-us/kb/311503;
– Using the Symbol Server technology
– Setting the _NT_SYMBOL_PATH environment variable
– Using the Microsoft Symbol Server with WinDbg
– Using the SymChk.exe utility to download symbols
In my version i choose the “Setting the _NT_SYMBOL_PATH environment variable”
set easy the Variable to the Environment with open a command prompt as admin
here are the parameters:
C:\
cd\
md symbols
Setx _NT_SYMBOL_PATH Symsrv*symsrv.dll*c:\symbols*http://msdl.microsoft.com/download/symbols /m
I used the Setx to set environment variables direct trough command line, don’t forget there is a /m in the end, you can do this also to remote computers have a look here for the full description: http://ss64.com/nt/setx.html
2. In the next step we would like install the TraceFMT.exe
in this case we need a tool from the Win10 Site: https://msdn.microsoft.com/en-US/windows/hardware/dn913721(v=vs8.5).aspx
I have downloaded the WDK and also the SDK for windows 10, just to be sure to have all tools ready.
in the end i found the TraceFMT.exe in the Source path here: “C:\Program Files (x86)\Windows Kits\10\bin\x64”
3. Open a command prompt with administrative rights.
4. Create a temporary folder, such as %systemdrive%\WULogs.
c:\
cd \
md WULogs
4. Locate the directory that contains Tracefmt.exe, as downloaded and installed in step 2. Then, copy Tracefmt.exe to %systemdrive%\WULogs.
cd C:\Program Files (x86)\Windows Kits\10\bin\x64
it’s a little tricky win10 command prompt can handle paths with spaces 🙂
copy tracefmt.exe c:\wulogs\
5. Run the following commands at a command prompt, in the order presented:
- cd /d %systemdrive%\WULogs
- copy %windir%\Logs\WindowsUpdate\* %systemdrive%\WULogs\
- tracefmt.exe -o windowsupate.log <each windows update log delimited by space> -r c:\Symbols
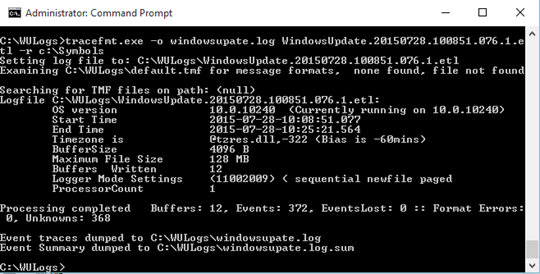
now you can open the Logfile, it’s created in C:\WULogs\windowsupdate.log
I know this as a little crapy, so just use the Powershell Command Let makes it easier for all 🙂
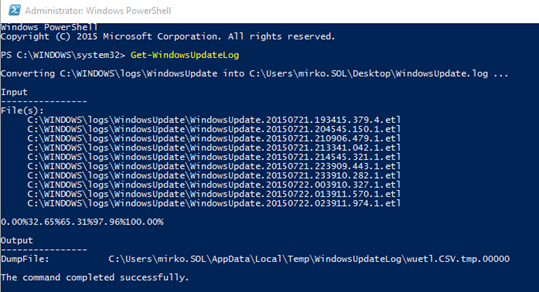
If you open it you see only a get-WindowsUpdateLog command for use in PoSh, hmm sounds interesting, open Powershell “as Admin” and type in the command
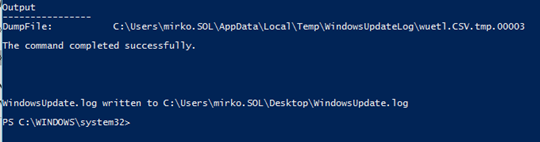
this command will generate a lot of Dump files and in the end they will merge all together:
The Log will be created in your users Profile an the Desktop, hmm
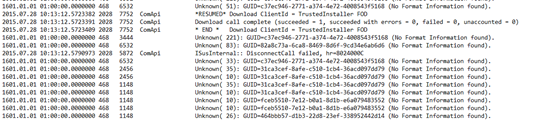
If you open the Log it’s difftent as the old one but you can still get the answers you need i think:
here the Get-Help commands from the new CMD-Let
NAME
Get-WindowsUpdateLog
SYNOPSIS
Merges Windows Update .etl files into a single log file.
SYNTAX
Get-WindowsUpdateLog [[-ETLPath] [<String[]>]] [[-LogPath] [<String>]] [[-SymbolServer] [<String>]] [-ForceFlush]
[-InformationAction {SilentlyContinue | Stop | Continue | Inquire | Ignore | Suspend}] [-InformationVariable
[<String>]] [-ProcessingType {CSV | XML}] [-Confirm] [-WhatIf] [<CommonParameters>]
DESCRIPTION
The Get-WindowsUpdateLog cmdlet merges and converts Windows Update .etl files into a single readable
WindowsUpdate.log file. Windows Update Agent uses Event Tracing for Windows (ETW) to generate diagnostic logs.
Windows Update no longer directly produces a WindowsUpdate.log file. Instead, it produces .etl files that are not
immediately readable as written.
This cmdlet requires access to a Microsoft symbol server.
RELATED LINKS
WindowsUpdate_Cmdlets
REMARKS
To see the examples, type: “get-help Get-WindowsUpdateLog -examples”.
For more information, type: “get-help Get-WindowsUpdateLog -detailed”.
For technical information, type: “get-help Get-WindowsUpdateLog -full”.
For online help, type: “get-help Get-WindowsUpdateLog -online”
Leave a Reply