now we would like to become the orange Belt, what that means in this Post of the EMS Belt series.
In the Earlier Post: http://blog.colemberg.ch/2015/01/ems-mdm-byod-mobile-wtf-yellow-belt/
I describes a little to begin a EMS, MDM, BYOD Project to be success in the end.
Nothing has changed this is my personal view about Mobile Device Management!
Next Step is to classified your Users, this is also a simple step or you can start a separate Project for this, but in our case we would not change the whole Company Security Policies.
Ok, in the most Companies we have the rule set of Policies, otherwise have a look to your Active Directory (on-premise), there should be a set of rights with User/Groups they have access to Files and folders or other services in your Domain, right?
In this case we would go a little deeper to details, we also have to reach a goal on the End-Devices.
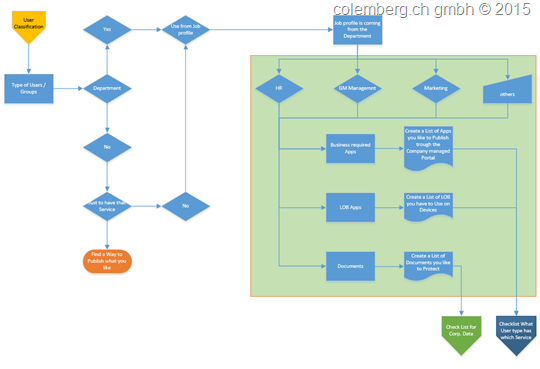
1. WE HAVE A BRAINSTORMING ABOUT “WE HAVE”
Users and Groups we have, at this time not rights and access, but to deliver a service in the end.
In this Case we come a little Back to the Corp. Data, How the Corp. Date to Protect, so we have different Users and also different “Confidential” Data to Protect from others…
As an Example: We have a Construction Engineer Team that create some stuff for a Patent. Now the Question: Is the Data from a Engineer more Important as the Data from the Team Leader for this Team?
The Answer: If you see the perspective from the Company, the Engineer have more Important Data, why, he has Data from the research to create a Patent and save the Company’s feature also save jobs. From another view the Team leader has some Data about the Engineer, that another Company can ask him to Join to work for the same Patent, and give him a better salary. OK the Answer for this Case is: Both Data are high risk Data and we have to Protect all of them.
2. Create a Matrix about your Employees
That is really a Easy job, isn’t it?
Go to your Active Directory, have a look on it and tell your self about the Matrix, have look on your Rights Management and maybe you can see what Data and which User are to Protect and let them run the right Application on a Device.
Here a little Helper to start that Process:
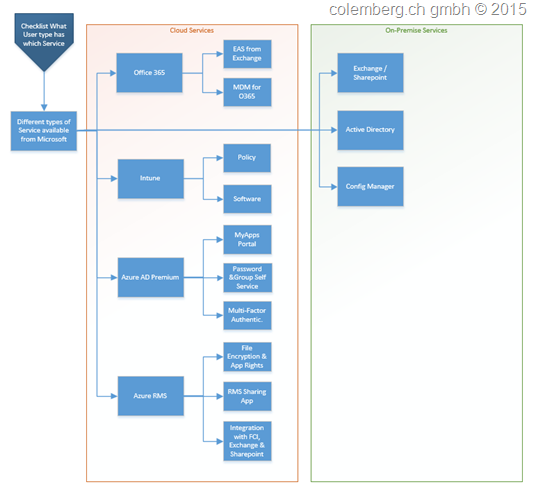
3. What User we have and What’s the Right Service
A Picture says more then 1000 Words.
This is just a Preview to the next Level for the User’s we have and what Service we become from Microsoft.
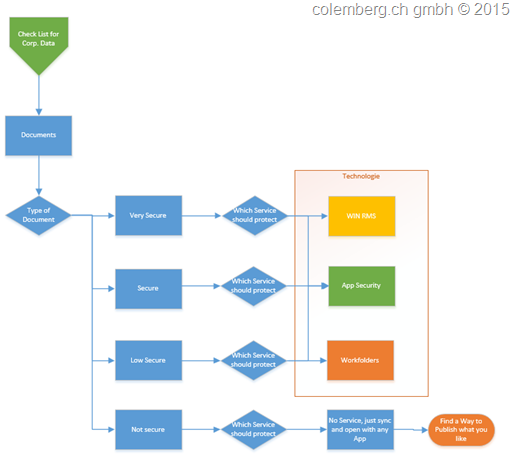
3. What Security Level of a Document we have
It is not that big question what secure Level we can protect our Documents, this is my view about this question and i think Microsoft has for every type the right Service available to use. OK now we can start a really hard Discussion about the Services behind a Security level, but i will tell you, why you have to study and spend a lot of money and wasting time to discus that with every Admin, Engineer or Manager? Keep it simple, the rule i have, use 20% effort to reach 80% from a goal.
In the Next Bolgpost we will Discuses in Detail about the Services and what possibilities we have in which Service, includes also the Documents.

Leave a Reply