Here we go for another Post!
This time, I tied to implement RBAC as a test and for a customer. It was quite hard to get the logic out of it and to figure out how it works in the backend. In the end, I got a piece of advice from a genius (thank you David Falkus https://github.com/davefalkus for your support) and after a short discussion, it made sense to me.
After searching on the internet, I found some docs from Microsoft. Unfortunately, there are not easy to understand, to make side notes or draw something. The document can be found here: https://docs.microsoft.com/en-us/intune/role-based-access-control
Therefore, I started my own logic draw and I would say it explains the topic in an easier way and I hope, it helps you to understand RBAC 😉
Overview
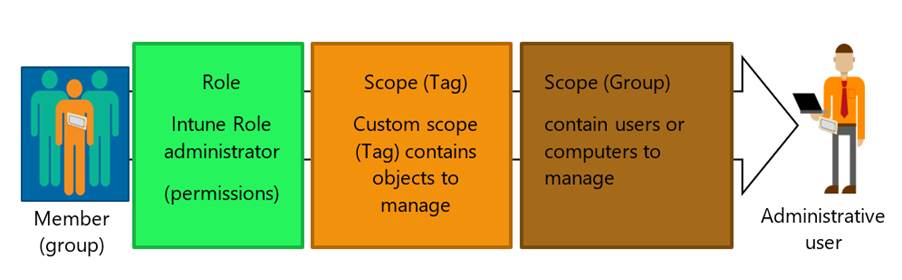
As you can see on the picture above, there are different parties involved:
- Member Group
- Role
- Scope Tag
- Scope Group
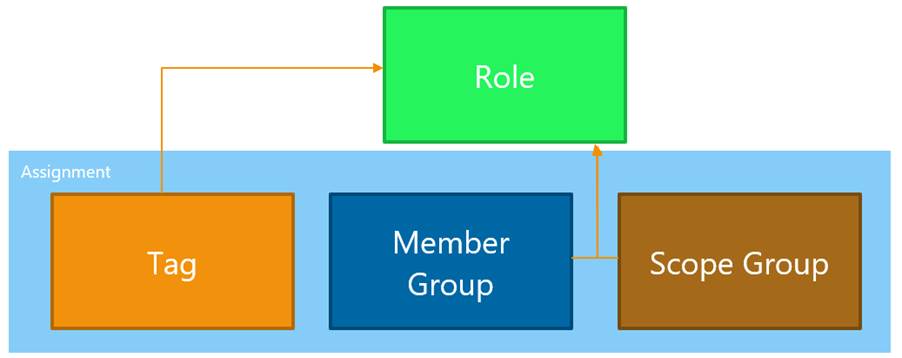
First, the whole configuration has to be configured with a role as a basis. Afterwards, it needs an assignment to add Tag, Member Group and Scope Group. You are able to use one role with the permission for multiple assignments for several use cases with the same rights.
Important: This is my own translation for the different parts in RBAC!
Scope Tags
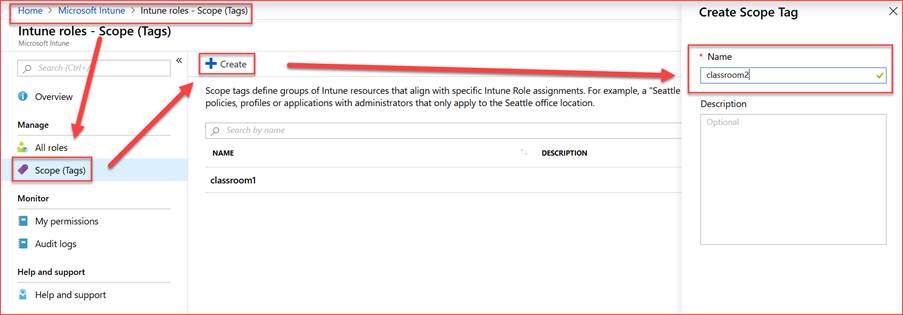
Tags are used to tag for example objects in Intune. These objects can be devices, policies, profiles and so on. If you have a group of device objects, you have to tag them separately. Unfortunately, there is no possibility of tagging a whole bunch of clients at the same time. In this case it is easier to use a script and do it with Graph API: https://github.com/microsoftgraph/powershell-intune-samples/tree/master/RBAC#12-rbac_scopetags_deviceunassignps1
Scope Group
Scope Group means that there are some users or devices to manage such as a limited group of objects like devices (iOS, Android or Windows) or only part of them such as all iOS from Marketing, etc.
Member Group
Member are one or a group of people who have to manage the objects in the Scope Group.
Role
Roles have different kinds of permissions. A role can have only “Read” rights on specific objects or “Write” or “Create” rights. We can for example grant access to create a new configuration profile or only change a Config profile with reading and writing access. A role can be used multiple times.
Assigenment
The Assignment contains Tags, Groups and Group Members. They are assigned to a role, which is able to only one or even multiple assignments.
How to Create the Parts
Scope Tags
Scope Group
Create a simple AAD Group (dynamic or static) with the objects you would like to manage.
Member Group
Create a simple AAD Group (dynamic or static) with the users, who have to manage the objects from the scope group.
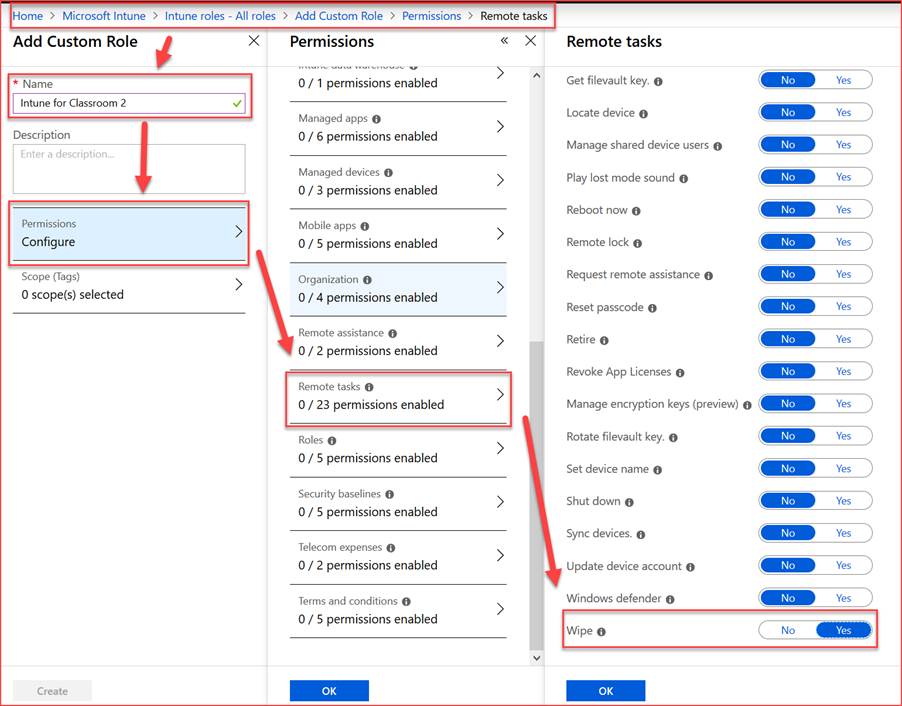
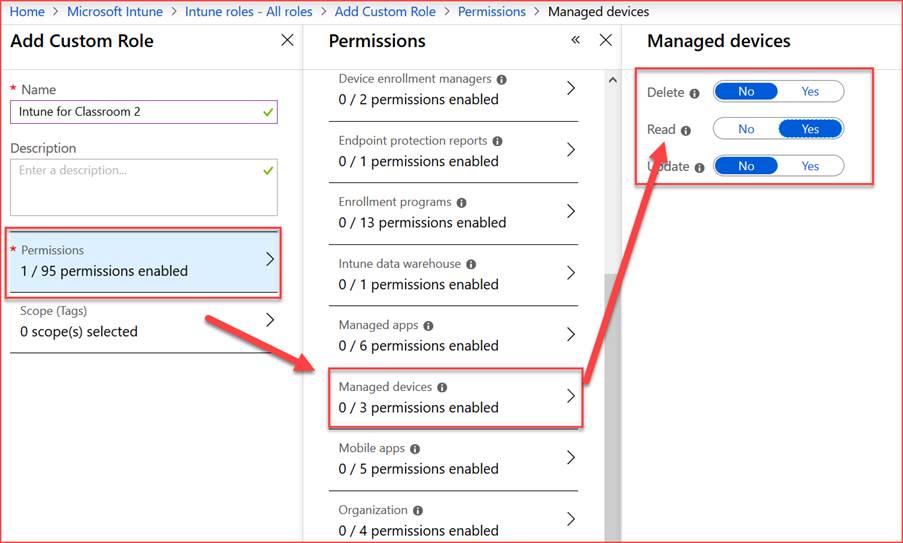
Role
Create permissions.
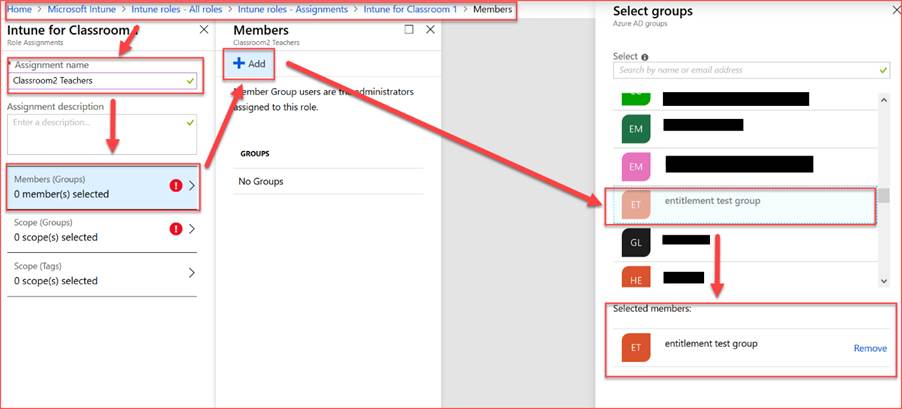
Assigenment
Add the member group to the assignment:
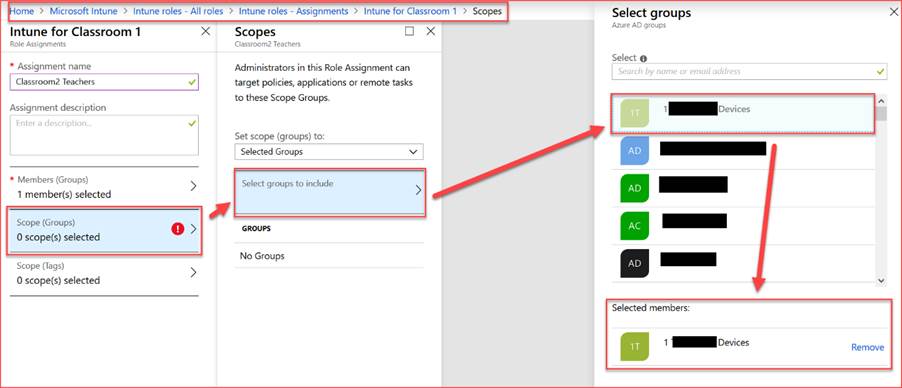
Add the Scope Group to the assignment:
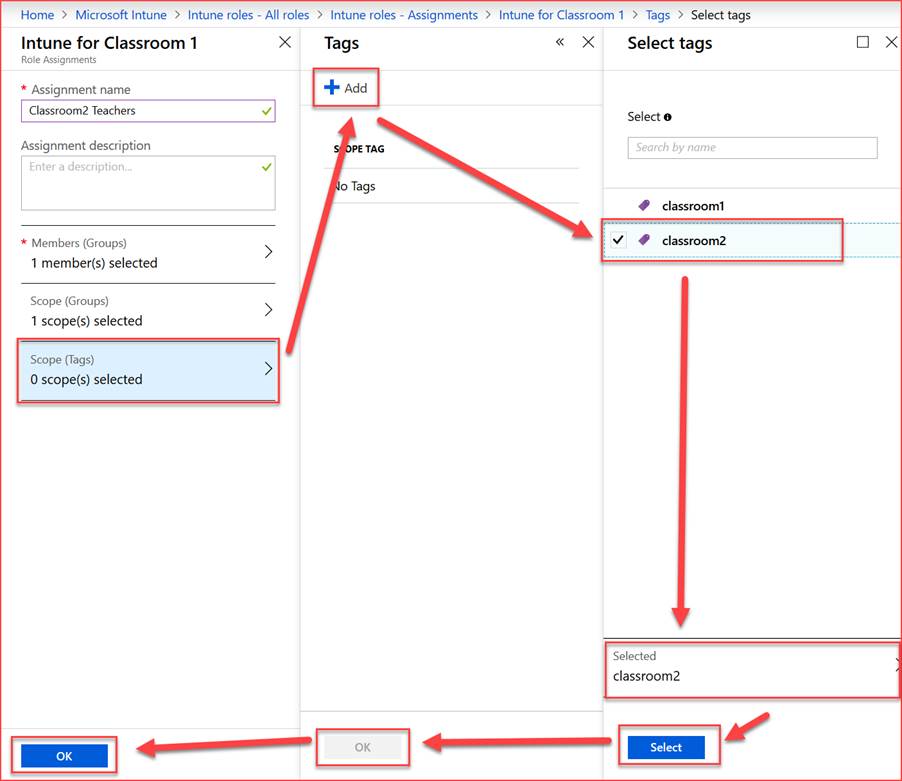
Add the Scope Tag to the assignment:
One last Thing:
Add a tag to a device:
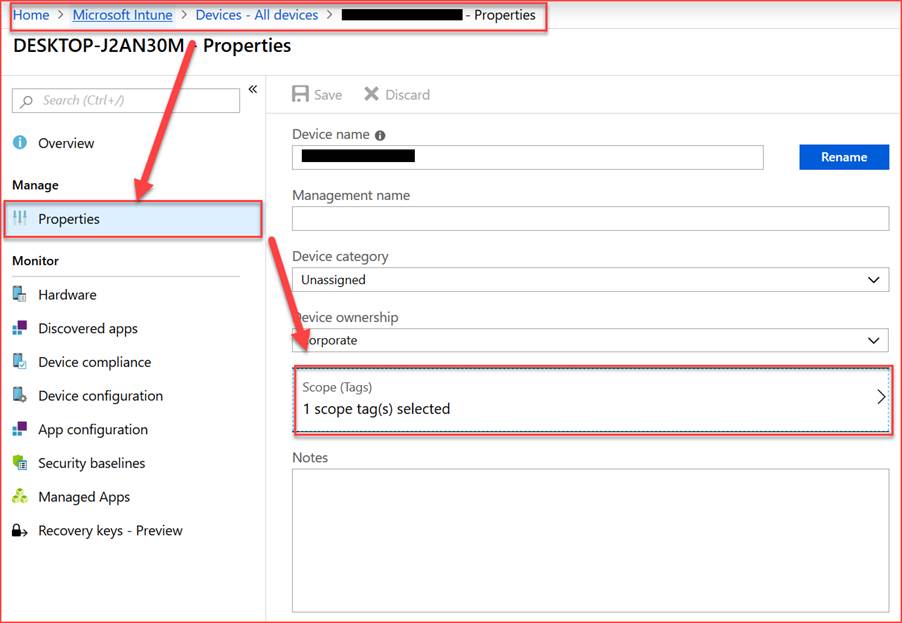
And this is it! Please be careful and test it only with a test user since you can exclude your own account from some config. I recommend using a global admin to create the whole RBAC. And avoid using a global admin in a member group. As well to point out: Never use all User & all Device for the Scope Group!
I hope this helps and saves you some time to have a beer….
Leave a Reply